The 2-Minute Rule for It Ot Cyber Security
Table of ContentsScada Ot Cybersecurity Things To Know Before You BuyThe 9-Minute Rule for Cyber Security Operational TechnologyOur Cybersecurity Ot DiariesAll about Scada Ot CybersecurityThings about Cyber Security Operational TechnologySee This Report about Ot CyberHow Operational Technology Cyber Security can Save You Time, Stress, and Money.
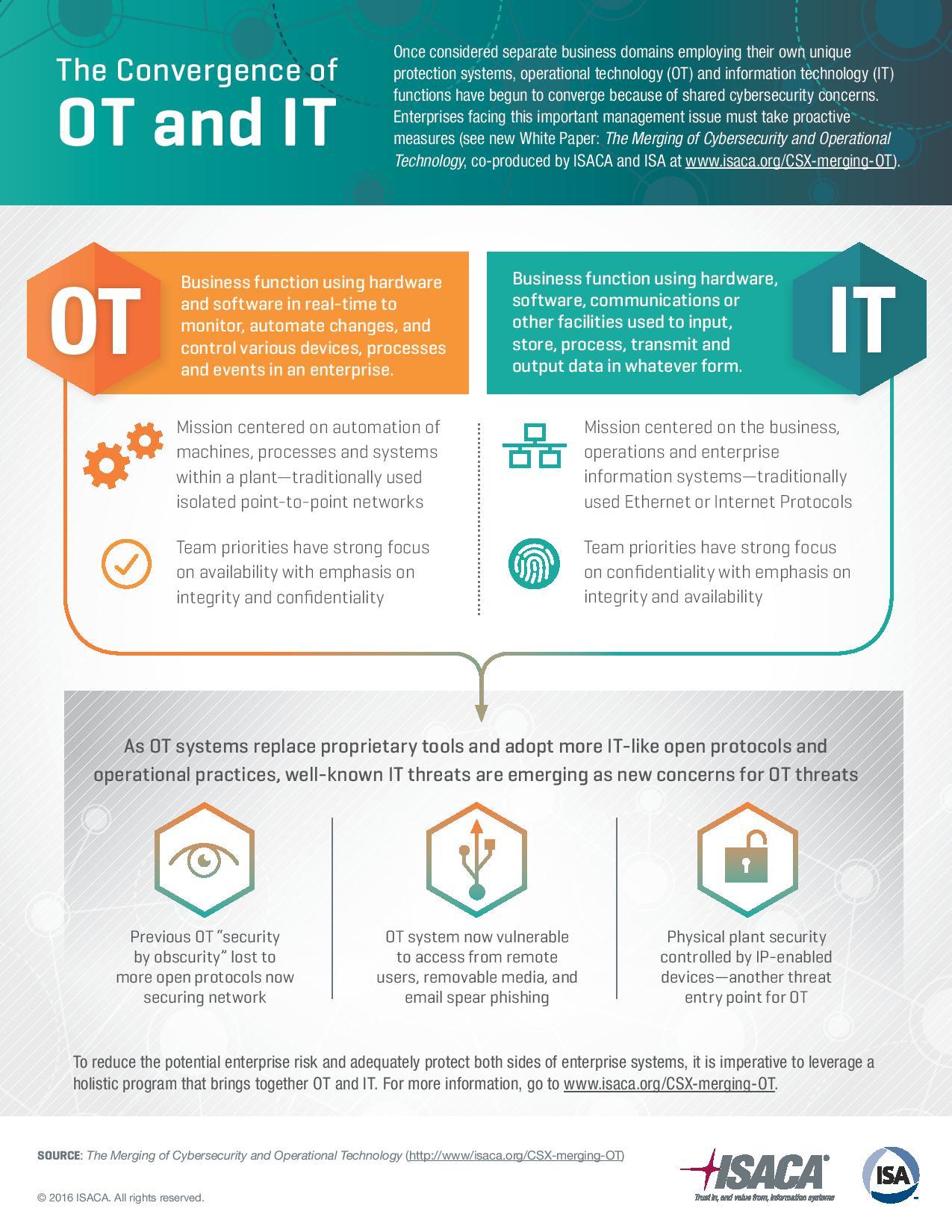
Depending on to the 2019 Ponemon Cyber Surveillance in Operational Modern Technology Report, over 60% of participants point out concern concerning an assault versus working technology (OT). Yet what is OT? When it concerns bodily tools, OT may be actually defined as a network-connected tool that keeps track of or even regulates procedures, as well as activities outside of Infotech (IT).
Cybersecurity pertains to technological and administration methods that defend bodies from assault. Along with OT cybersecurity, these procedures include the breakthrough, tracking, and remediation of network-connected OT devices had an effect on by unique actions. The rise of OT devices made use of in industries such as healthcare as well as life sciences has produced OT cybersecurity much more important.
The Ot Cyber Ideas
And requests of OT in smart buildings that utilize wireless devices to observe and control systems including heating system, air flow, as well as sky conditioning (HVAC) rely upon tough OT cybersecurity. Compare to OT cybersecurity, IT staffs focus less on device strength and also more on the integrity of relevant information. Thereby, IT teams as well as OT groups might possess various top priorities.
The issue along with OT cybersecurity is that a lot of equipments are operating out-of-date program, or they might lack after-market security patches. This gives cyberpunks an also higher opportunity to compromise them or corrupt them along with malware and interfere with procedures. Windows vulnerabilities like BlueKeep and also DejaBlue continue to be actually uncovered in old Windows systems. Cysol Networks.
The Ultimate Guide To Ot In Cyber Security
Depending on to the 2020 Worldwide Risk Record through OT safety and security firm CyberX, unsupported as well as unpatched system software including Microsoft window XP, Windows 2000, and now Microsoft window 7 represent 71% of systems they analyzed. When an OT cybersecurity event takes place, the security staff might possess little to no situation about the tool.
Yet tool proprietor, location, utilization, software application model and also most recent servicing report may be actually skipping. When this occurs, there's a danger that the wrong removal steps are actually taken, such as separating a medical unit. In a field including healthcare, it is actually critical that a licensed clinical engineer is actually sent off to remediate the gadget.
The Only Guide to Operational Technology Cyber Security
To deal with these OT cybersecurity problems, what is actually needed is the capability to track and keep a precise stock of OT properties as well as the details about them. When a device is actually acquired as well as provisioned, the gadget expert or a 3rd celebration industry specialist must have the capacity to input the gadget particulars into the stock when they function in-person or from another location on the gadget.
This device stock serves as the singular source of fact that obtains an improve when routine servicing happens, where workers are going to improve the device records along with any kind of brand-new relevant information. But past tool invention and developed gadget records, there need to be actually security orchestration, hands free operation, and action procedure and also device of report where the stock as well as surveillance activities records may be actually taken in (Cysol Networks).
Getting The Cyberx Ot To Work
When a surveillance event occurs, the surveillance staff may see the full context of the gadget. They'll understand that the tool proprietor is actually and also what remediation process should be actually adhered to so a job order could be sent off to the unit designer, or suppliers or provider industry service technician. And also the work purchase procedure could be tracked in order that protection, IT, and also the device engineers are actually https://cysol-networks.com/ maintained familiar with the removal standing.
That is actually given that Nuvolo becomes the system of report. Nuvolo will certainly take in security details, compare the device's IP and MAC handle, as well as fully contextualize it with traits like the unit consumption, what PHI data the unit is actually stashing or even accessing, as well as gadget upkeep documents. Nuvolo's OT Safety and security platform, when incorporated with real-time https://en.search.wordpress.com/?src=organic&q=cyber security surveillance units supplies the security and service monitoring crews discussed exposure right into gadget pose.
The Ultimate Guide To Ot In Cyber Security
In pioneering the business's 1st OT cybersecurity answer improved ServiceNow, Nuvolo aids customers achieve better item, facility, as well as person security while protecting critical infrastructure. You may view a full trial on just how OT Cyber can easily help you manage your non IT hooked up tools by contacting us below https://www. nuvolo.com/product-walkthrough/.
It is actually with growing worry that cyberpunks are significantly targeting ), crucial for supply, production as well as protection of. Assaults versus OT have enlarged in the final few years. Power providers help make up a bulk of these attacks a spike steered by growing older properties, old safety and security techniques and also increased connectivity.
Not known Incorrect Statements About Cybersecurity Ot
This research covers subject matters like: The brand new threat frontier in the energy field and what the sector need to carry out to ready. The connection in between connectivity, transparency and also insight. Why safety analytics are a vital part of any sort of institution.
Gartner determines OT protection as, "Practices and also technologies used to (a) secure people, possessions, and also details, (b) screen and/or management bodily units, procedures and activities, and (c) start condition changes to company OT devices." OT security answers include a vast array of protection innovations coming from next-generation firewall programs (NGFWs) to security info as well as event control (SIEM) bodies to identity get access to as well as control, and so much more - Cysol Networks.